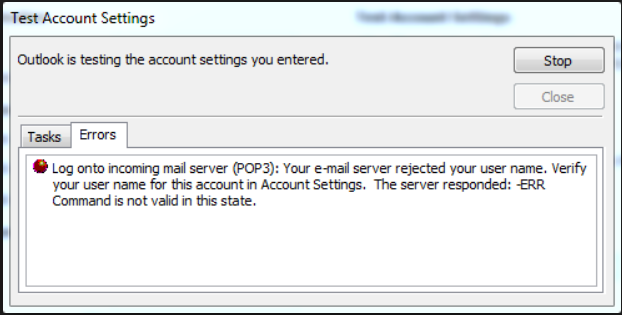
Below is the error message while configuring the outlook POP for the Exchange 2013 user. Exchange 2013 with CAS and MBX installed separately.
Assessment/Troubleshooting:
- POP services are enabled on the servers and for the user
-
Ran the below command to check the server component state and POP was Active
Get-Servercomponentstate –server “servername”
-
Checked the Server health report for POP.protocol health set and the below probes were unhealthy
PopSelfTestProbe
PopDeepTestProbe
-
Ran the command,
Invoke-MonitoringProbe POP.Protocol\PopSelfTestProbe -Server “Servername” | Format-List
- Got the error “Unable to initialize TCP Network connection”
- Enabled the protocol logging on the CAS server and got the below error in the protocol logs
22T07:30:46.994Z,0000000000000003,2,127.0.0.1:993,127.0.0.1:32258,username,1196,78,97,login,[email protected] *****,”R=””z NO [Error=ProxyNotAuthenticated Proxy=EXCHANGESERVER.DOMAIN.COM:1995:SSL] LOGIN failed.””;Msg=Proxy:EXCHANGESERVER.DOMAIN.COM:1993:SSL;ErrMsg=ProxyNotAuthenticated”
- Checked the certificate on the “Exchange Backend website” on the Mailbox servers and the self-signed certificate was assigned properly
Solution:
-
Found that X509CertificateName was set to the third party certificate pointing to webmail.domain.com on the mailbox servers as well
Get-popsettings –server “mailboxservername” | fl
-
Changed it to the self-signed certificate of the mailbox server,
Set-popsettings –server “mailboxservername” –X509CertificateName “mailboxservername”
- Restarted the POP services on the CAS & mailbox servers
- Get-service “*POP*” –computername “servername” | Restart-Service
- Tried configuring the outlook POP profile and it was successful
Thoughts:
In Exchange 2013, both the Mailbox and CAS roles come with a default SAN certificate configured during the install. The self-signed certificate on the CAS server should be replaced by a third party or an internal PKI certificate as part of the configuration. The default certificate on the mailbox role is used to encrypt the communication between the CAS and the Mailbox server. Since the certificate is created and signed by Exchange, all Exchange servers in your organization including the CAS will trust it automatically. This is the reason why clients won’t receive a pop up saying the certificate is not trusted, even though the mailbox role is responsible for everything to do with the user’s mailbox. Hence, you don’t need a third party or internal PKI certificate. You shouldn’t delete it, as it will break your secure client communication through the CAS. No additional configuration is required on this certificate either.
References:
https://technet.microsoft.com/en-us/library/ms.exch.scom.pop(v=exchg.150).aspx
http://clintboessen.blogspot.ae/2018/03/binding-certificate-breaks-imap-or-pop.html
https://cloudiffic.com/exchange-2013-certificate-on-mailbox-role/
Happy learning!! 🙂