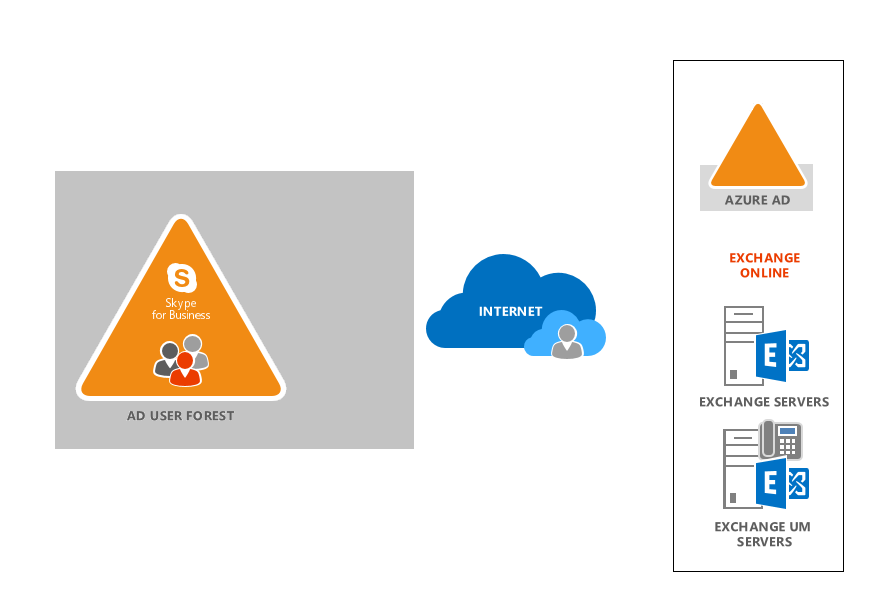
Skype for Business & Exchange Online Oauth Configuration.
Skype for business server need to communicate safely and securely with other application and servers. The server at other end can be Office Web Apps Server/ an Exchange server or any other application that need to securely communicate with Skype for Business. Oauth is a better and more efficient approach is to use a standardized method for all server-to-server authentication and authorization. With Oauth, user credentials and passwords are not passed from one computer to another. Instead, authentication and authorization is based on the exchange of security tokens; these tokens grant access to a specific set of resources for a specific amount of time. OAuth authentication typically involves three parties: a single authorization server and the two parties(servers) that need to communicate with one another. Security tokens will be issued by the authorization server to the two servers that need to communicate; these tokens verify that communications originating from one server should be trusted by the other realm. For Skype for Business online Server to communicate with its Exchange counterpart, Skype for Business Server 2015 must first obtain a security token from the authorization server. Skype for Business Server then uses that security token to identify itself to Exchange. The Office 365 version of Exchange must go through the same process in order to communicate with Skype for Business Server 2015.
Note: For on-premises server-to-server authentication between two Microsoft servers there is no need to use a third-party token server. Skype for Business Server 2015 and Exchange 2013 have a built-in token server that can be used for authentication purposes with other Microsoft servers such as SharePoint that support server-to-server authentication.
Skype for Business Server 2015 supports three server-to-server authentication scenarios. With Skype for Business Server 2015 we can do:
- Server-to-server authentication between an on-premises installation of Skype for Business Server 2015 and an on-premises installation of Exchange 2013 and/or SharePoint Server.
- Configure server-to-server authentication between a pair of Office 365 components(With in O365)
- Configure server-to-server authentication in a hybrid environment.
Configuration steps:
Step1: Find the Display name of the Tenant.
Get-Cstenant, Make a note of the display name. (From MSOL powershell)
Step2: From Skype for business shell run below cmd. Configuring SFB to use O365 Oauth server.
New-CsOAuthServer microsoft.sts -MetadataUrl “https://accounts.accesscontrol.windows.net/“Displayname”/metadata/json/1″
Step3: Remove any Partner application with name microsoft.exchange in current settings.
Run Get-CsPartnerApplication “microsoft.exchange”, If you get some result proceed with Step4 else go to Step5.
Step4: Remove the existing Partner application.
Remove-cspartnerapplication “Microsoft.Exchange”
Step5: Create a new partner application
New-CsPartnerApplication -Identity microsoft.exchange -ApplicationIdentifier 00000002-0000-0ff1-ce00-000000000000 -ApplicationTrustLevel Full -UseOAuthServer
Now SFB on-premise is configured to use Office 365 Oauth servers, that means O365 Auth server will be issuing tokens to SFB server which sfb server should be presenting to O365 exchange.
Next we need to create a trust between on premise and Office 365.
Step6: From MSO powershell
Import-module MSOnlineExtended
Step7: Find the MSOLServicePrincipal name for Skype for business server.
Get-MSOLServicePrincipal | FL displayplayname
Step8: Export the existing Oauth cert in Skype for business server as X.509 Base64
Step9: Run below script to get all the variables as below.
$certificate = New-Object System.Security.Cryptography.X509Certificates.X509Certificate
$certificate.Import(“C:\Users\annop\SFBOauth.cer”)
$binaryValue = $certificate.GetRawCertData()
$credentialsValue = [System.Convert]::ToBase64String($binaryValue)
Step10:
The New-MsolServicePrincipalCredential cmdlet can be used to add a new credential to a service principal or to add or roll credential keys for an application. The service principal is identified by supplying one of the following: object ID, appPrincipalID, service principal name (SPN). In this case we had used AppPrincipalID(default value)
New-MsolServicePrincipalCredential -AppPrincipalId 00000004-0000-0ff1-ce00-000000000000 -Type Asymmetric -Usage Verify -Value $credentialsValue -StartDate 02/04/2016 -EndDate 01/04/2017
StartDate: The effective start date of the credential usage. The default start date value is today. For an “asymmetric” type credential, this must be set to on or after the date that the X509 certificate is valid from, otherwise an OAuth token will not be issued for this application.
The default setting is
Required? false
Position? named
Default value Today
Accept pipeline input? true (ByPropertyName)
Accept wildcard characters? false
EndDate: The effective end date of the credential usage. The default end date value is one year from today. For an “asymmetric” type credential,this must be set to on or before the date that the X509 certificate is valid until, otherwise an OAuth token will not be issued for this application.
The default setting is
Required? false
Position? named
Default value Today + 1 year
Accept pipeline input? true (ByPropertyName)
Accept wildcard characters? False
Type: The type of credential used. The credential type can either be set to “asymmetric”, “symmetric” or “password”.
The default setting is “symmetric”.
Required? false
Position? named
Default value symmetric
Accept pipeline input? true (ByPropertyName)
Accept wildcard characters? False
Step11: From Lync Poweshell set Autodiscoverurl. (We use http, since O365 is multitenant)
Set-CSOauthConfiguration -Identity Global -ExchangeAutodiscoverurl “http://autodiscover.cloudexchangers.com/autodiscover/autodiscover.svc“
Oauth Setup Renewal
You need to remove the MSOLServicePrincipal each time the setup expires and then replace it with your new certificate following same steps 8,9,10.
If you have any suggestions or feedback, please feel free to comment below.
Happy Learning..!!!
Anoop Karikuzhiyil Babu
Reference:
https://technet.microsoft.com/en-us/library/jj204817.aspx?f=255&MSPPError=-2147217396
[…] again, another blog post from Cloud Exchangers about OAuth is very useful to implement […]
[…] http://cloudexchangers.com/skypeforbusinessoauthwitho365/ […]