Microsoft has detected multiple 0-day exploits being used to attack on-premises versions of Microsoft Exchange Server in limited and targeted attacks. In the attacks observed, the threat actor used these vulnerabilities to access on-premises Exchange servers which enabled access to email accounts and allowed installation of additional malware to facilitate long-term access to victim environments.
For the past few weeks, Microsoft and others in the security industry have seen an increase in attacks against on-premises Exchange servers. The target of these attacks is a type of email server most often used by small and medium-sized businesses, although larger organizations with on-premises Exchange servers have also been affected. Exchange Online is not vulnerable to these attacks.
The first step is making sure all relevant security updates are applied to every system. Find the version of Exchange Server you are running and apply the update.
The next critical step is to identify whether any systems have been compromised, and if so, remove them from the network. Microsoft has released the scripts and tools to scan for signs of compromise.
HAFNIUM:
HAFNIUM has previously compromised victims by exploiting vulnerabilities in internet-facing servers, and has used legitimate open-source frameworks, like Covenant, for command and control. Once they’ve gained access to a victim network, HAFNIUM typically exfiltrates data to file sharing sites like MEGA.
Affected versions:
The vulnerabilities affect Exchange Server versions 2013, 2016, and 2019, while Exchange Server 2010 is also being updated for defense-in-depth purposes. Exchange Online is not affected.
CVE Details:
|
CVE |
Description |
Impact |
| CVE-2021-26855 | server-side request forgery (SSRF) vulnerability in Exchange which allowed the attacker to send arbitrary HTTP requests and authenticate as the Exchange server | Gain access to mailboxes, read the full contents. |
| CVE-2021-26857 | insecure deserialization vulnerability in the Unified Messaging service. Insecure deserialization is where untrusted user-controllable data is deserialized by a program. Exploiting this vulnerability gave HAFNIUM the ability to run code as SYSTEM on the Exchange server. This requires administrator permission or another vulnerability to exploit. | Arbitrary code execution as SYSTEM user, compromise the system |
| CVE-2021-26858 | a post-authentication arbitrary file write vulnerability in Exchange. If HAFNIUM could authenticate with the Exchange server then they could use this vulnerability to write a file to any path on the server. They could authenticate by exploiting the CVE-2021-26855 SSRF vulnerability or by compromising a legitimate admin’s credentials. | Arbitrary code execution, compromise the system |
| CVE-2021-27065 | post-authentication arbitrary file write vulnerability in Exchange. If HAFNIUM could authenticate with the Exchange server then they could use this vulnerability to write a file to any path on the server. They could authenticate by exploiting the CVE-2021-26855 SSRF vulnerability or by compromising a legitimate admin’s credentials. | Arbitrary code execution, compromise the system |
Mitigation:
- Install the security patch
Exchange 2019, 2016, 2013 – KB5000871
- Download here – KB5000871
Exchange 2010 – KB5000978
- Download here
Installation steps:
- Download the update but do not run it immediately.
- Temporarily disable file-level antivirus software
- Select Start, and type CMD.
- In the results, right-click Command Prompt, and then select Run as administrator.
- If the User Account Control dialog box appears, choose Yes, and then select Continue.
- Type the full path of the .msp file, and then press Enter.
- After the installation is finished, re-enable the antivirus software, and then restart the computer. (You might be prompted by the installer to restart.)
Exploitation of the security vulnerabilities addressed in these fixes requires HTTPS access over the Internet. Therefore, our recommendation is to install the security updates first on Exchange servers exposed/published to the Internet (e.g., servers publishing Outlook on the web/OWA and ECP) and then update the rest of your environment. While those security updates do not apply to Exchange Online / Office 365, you need to apply those Security Updates to your on-premises Exchange Server, even if it is used for management purposes only.
How to check the logs for any malicious activity:
This script checks targeted exchange servers for signs of the proxy logon compromise. Proxy logon vulnerabilities are described in CVE-2021-26855, 26858, 26857, and 27065. This script is intended to be run via an elevated Exchange Management Shell.
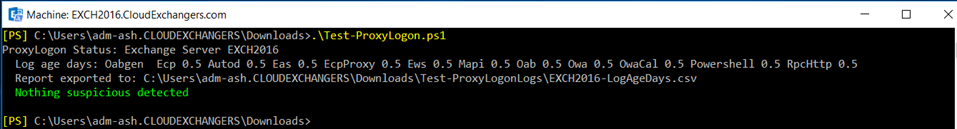
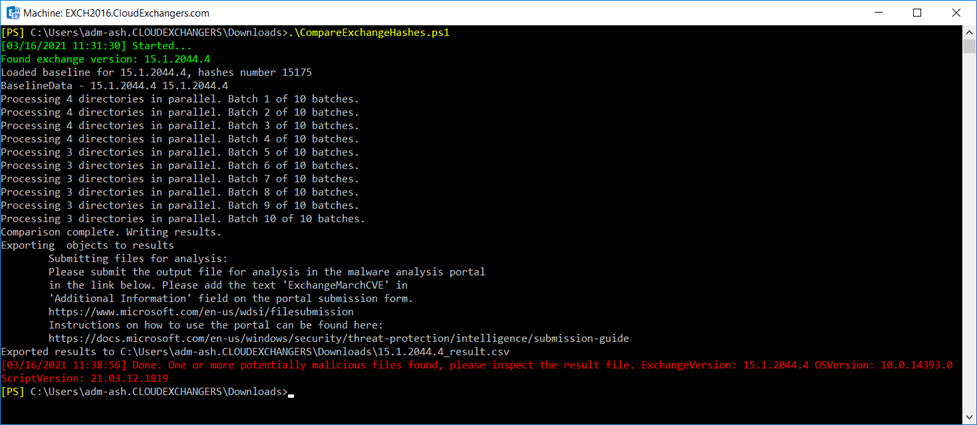
This script checks file hashes in exchange vdirs against known good baseline of hashes and any file under IIS root which is edited after Dec 1st 2020 is marked as suspicious.
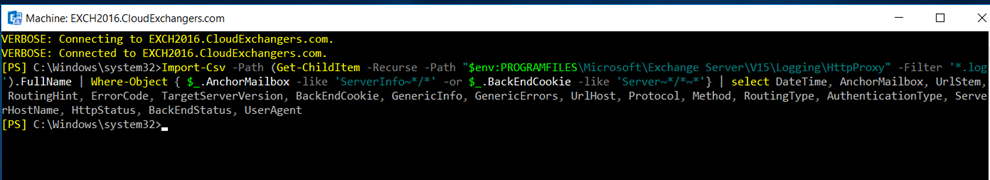
Scan Exchange log files for indicators of compromise:
- Exchange HttpProxy logs checks
Import-Csv -Path (Get-ChildItem -Recurse -Path “$env:PROGRAMFILES\Microsoft\Exchange Server\V15\Logging\HttpProxy” -Filter ‘*.log’).FullName | Where-Object { $_.AnchorMailbox -like ‘ServerInfo~*/*’ -or $_.BackEndCookie -like ‘Server~*/*~*’} | select DateTime, AnchorMailbox, UrlStem, RoutingHint, ErrorCode, TargetServerVersion, BackEndCookie, GenericInfo, GenericErrors, UrlHost, Protocol, Method, RoutingType, AuthenticationType, ServerHostName, HttpStatus, BackEndStatus, UserAgent
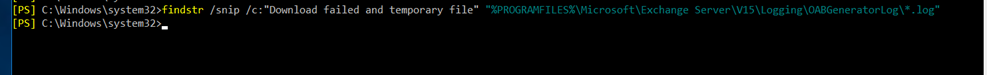
- Check for OABGen File
findstr /snip /c:”Download failed and temporary file” “%PROGRAMFILES%\Microsoft\Exchange Server\V15\Logging\OABGeneratorLog\*.log”
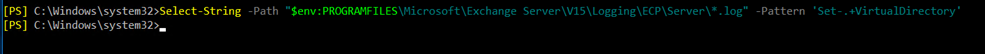
- Exchange log files for ECP
Select-String -Path “$env:PROGRAMFILES\Microsoft\Exchange Server\V15\Logging\ECP\Server\*.log” -Pattern ‘Set-.+VirtualDirectory’
Download here
- Microsoft Support Emergency Response Tool (MSERT) to scan Microsoft Exchange Server
Microsoft Defender has included security intelligence updates to the latest version of the Microsoft Safety Scanner (MSERT.EXE) to detect and remediate the latest threats known to abuse the Exchange Server vulnerabilities.
Download here
Remediate any identified exploitation or persistence:
If you find any evidence of exploitation (e.g., in Exchange application logs), ensure you are retaining the logs, and use the details such as timestamps and source IPs to drive further investigation.
If you find known bad files using your endpoint security solution, the Microsoft IOC feed, or the Microsoft Safety Scanner, take the following actions:
-
Remediate and quarantine them for further investigation unless they are expected customizations in your environment.
-
Search your IIS logs to identify whether or not the files identified as malicious have been accessed.
-
Consider submitting suspected malicious files to Microsoft for analysis following this guidance: Submit files for analysis by Microsoft – Windows security | Microsoft Docs and include the string “ExchangeMarchCVE” in the Additional Information text box of the submission form.
References: https://www.microsoft.com/security/blog/2021/03/02/hafnium-targeting-exchange-servers/
Happy learning!! 🙂
