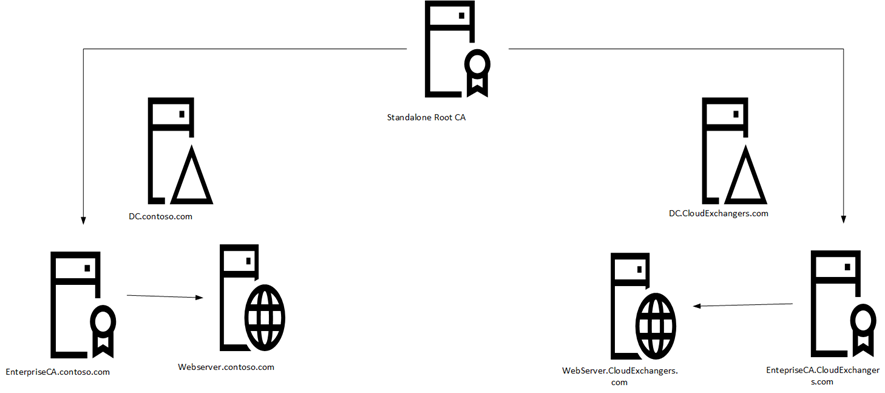
In this post, I would like to share with you the steps I carried out to implement the Multi Forest two-tier PKI infrastructure with Windows server 2016 without the Active Directory trust. There is information available to implement the two-tier PKI in a single forest and cross forest deployments. However, this deployment is with no support for cross-forest certificate enrollment, AD CS deployed in each forest. A standalone root CA deployed to be a central trusted root for the PKI and domain members in all forests. The enterprise CA certificates in each forest and all certificates issued to domain members in all forests have a certification path ending at the trusted root CA certificate.
In this lab, we will be using the below infrastructure,
|
Forest A: Contoso.com |
|
| Domain Controller | 10.0.0.2 |
| Enterprise Issuing CA | 10.0.0.3 |
| WebServer | 10.0.0.4 |
|
Forest B: CloudExchangers.com |
|
| Domain Controller | 10.10.10.10 |
| Enterprise Issuing CA | 10.10.10.11 |
| WebServer | 10.10.10.12 |
| Offline Root CA | WorkGroup |
All the servers are windows server 2016 standard. I have implemented this with the default configuration and hence I haven’t used CAPolicy.inf
Standalone Root CA Installation
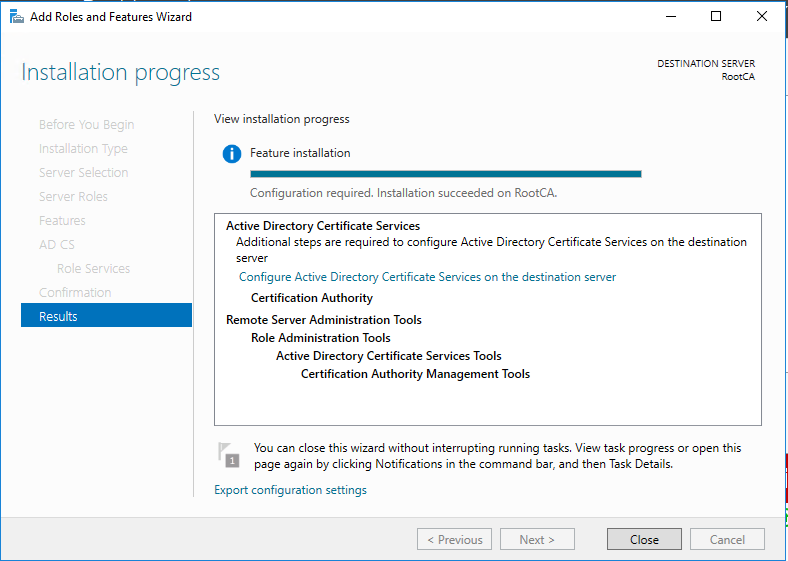
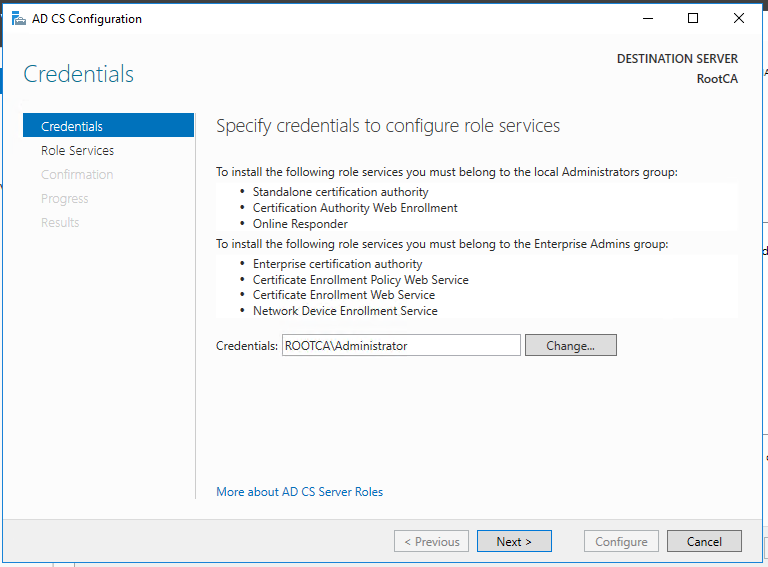
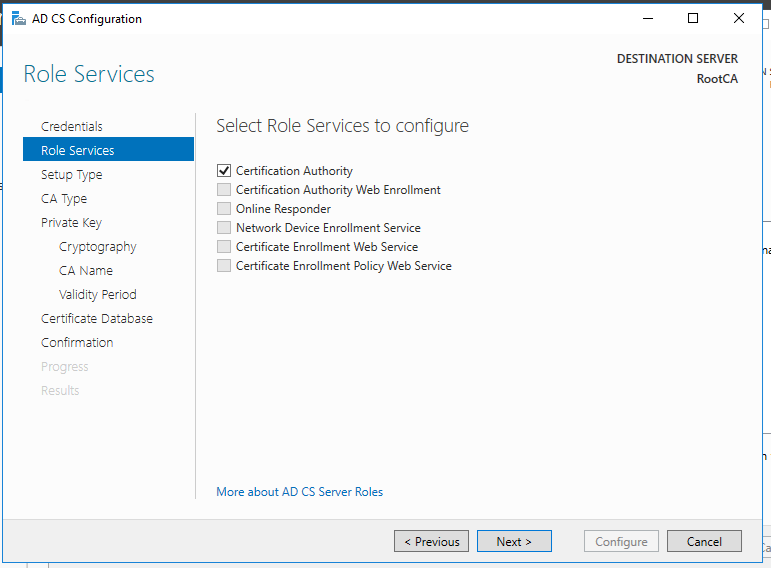
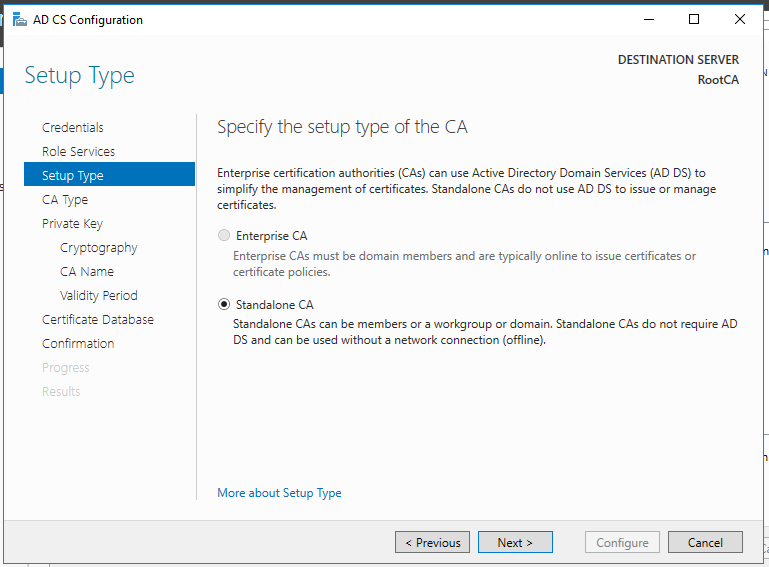
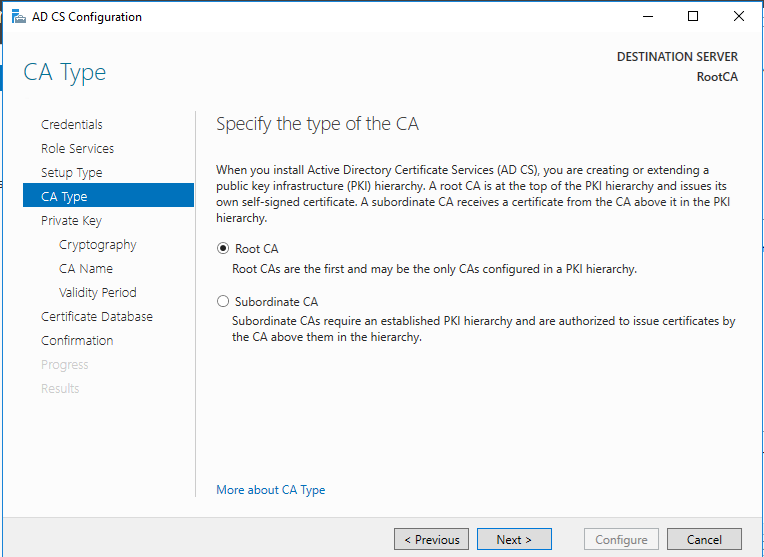
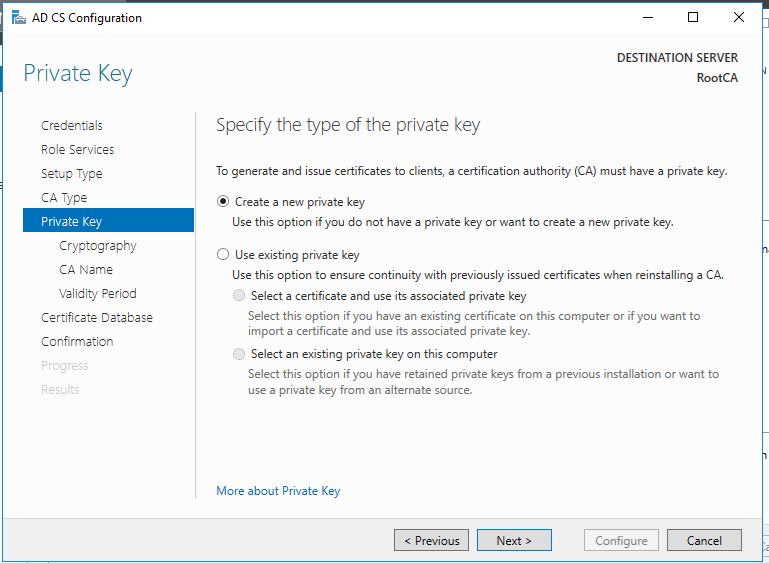
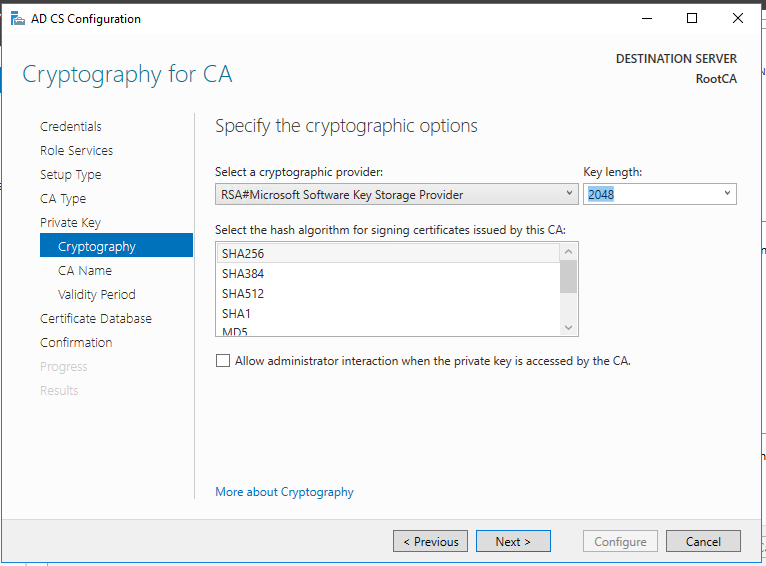
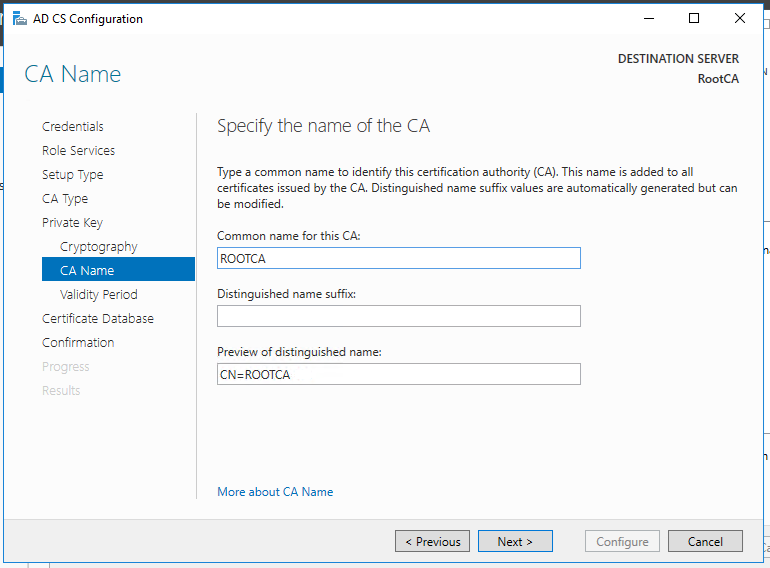
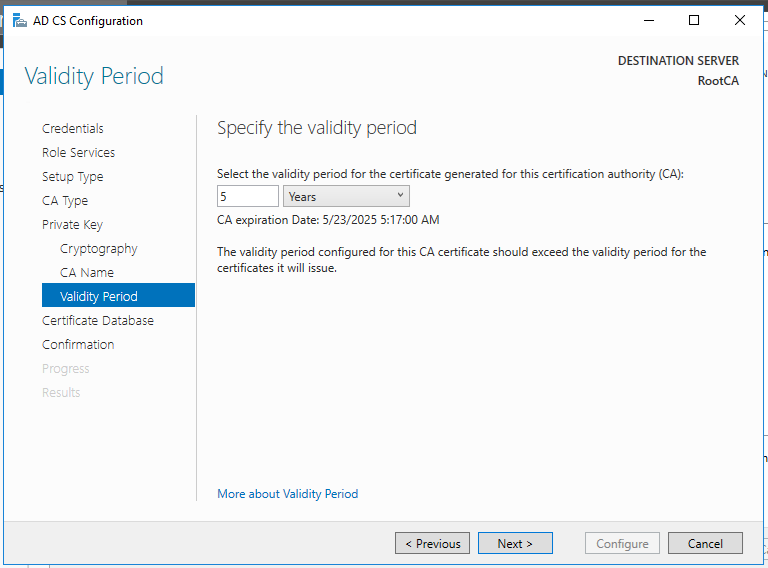
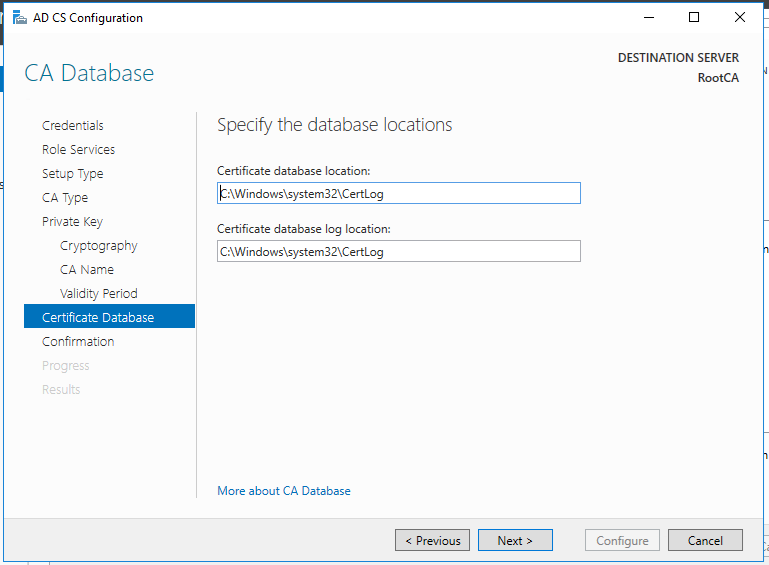
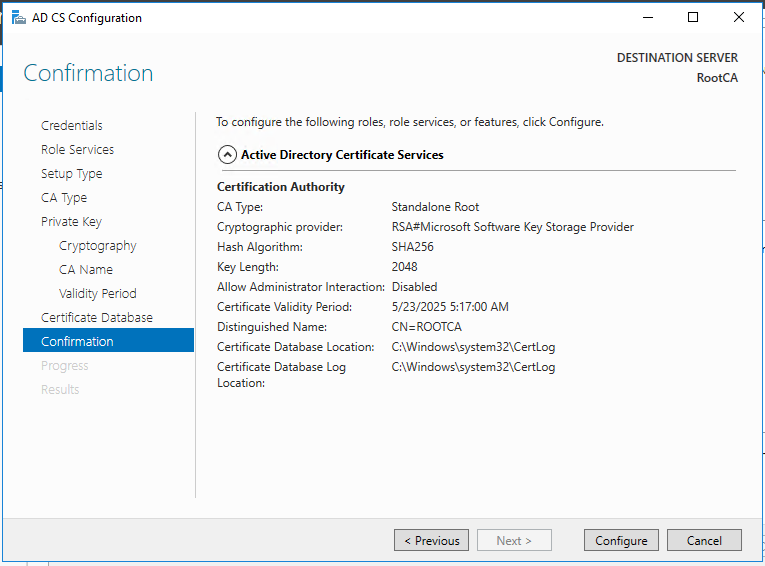
So, now we have the functional standalone Root CA. There are some post deployment configuration needs to be done.
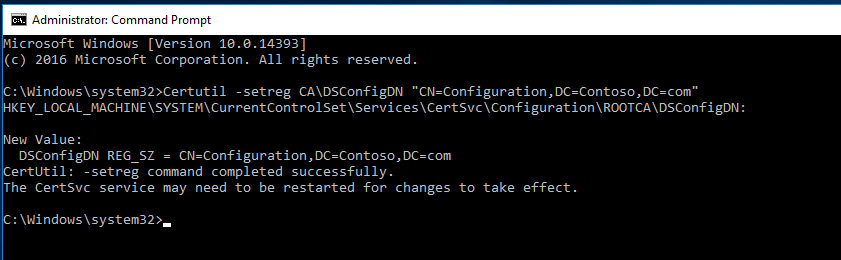
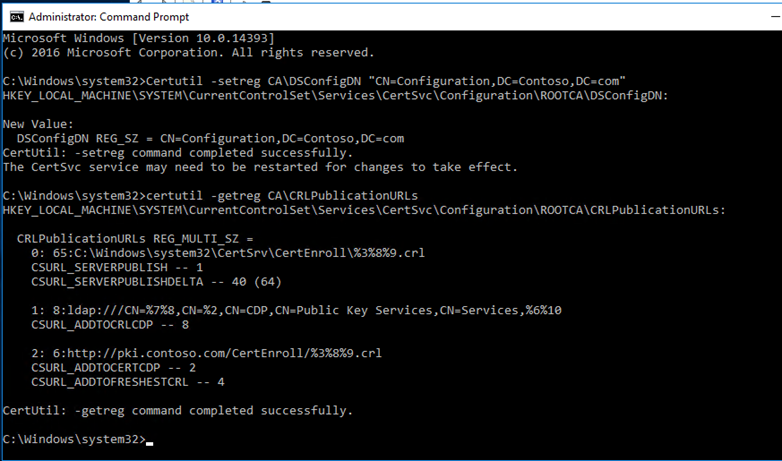
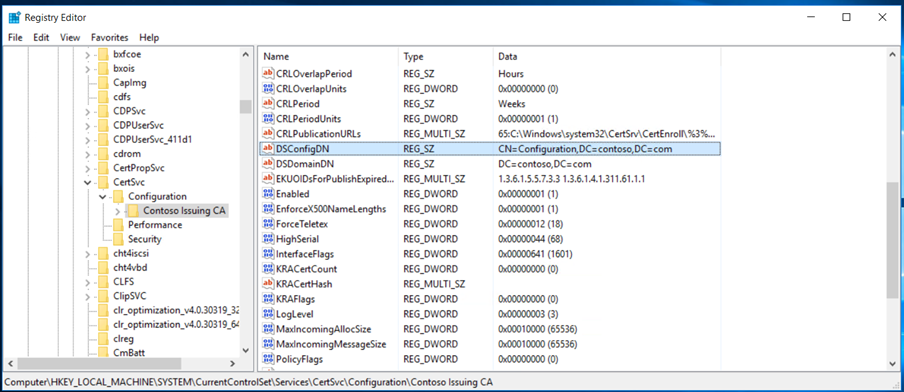
DSConfigDN
Standalone root CA is not part of the domain and will be put offline, we will need to publish the CRL and AIA files to a custom URL hosted by web server. For that, we need to run the below command.
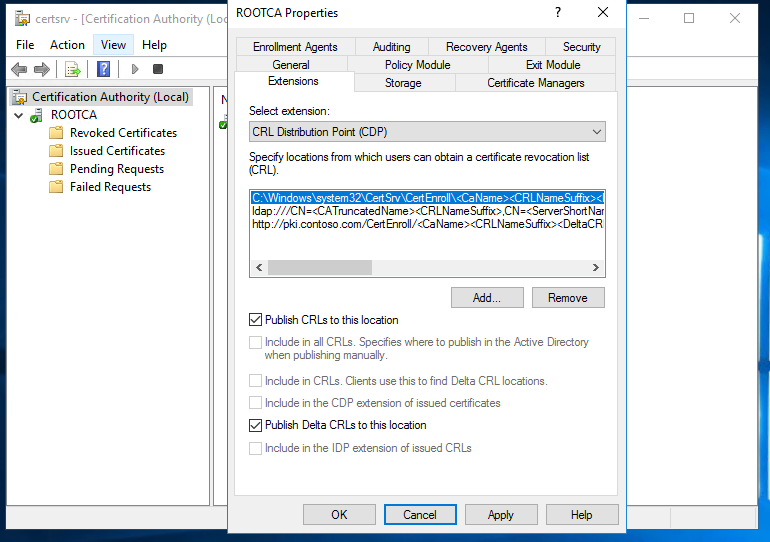
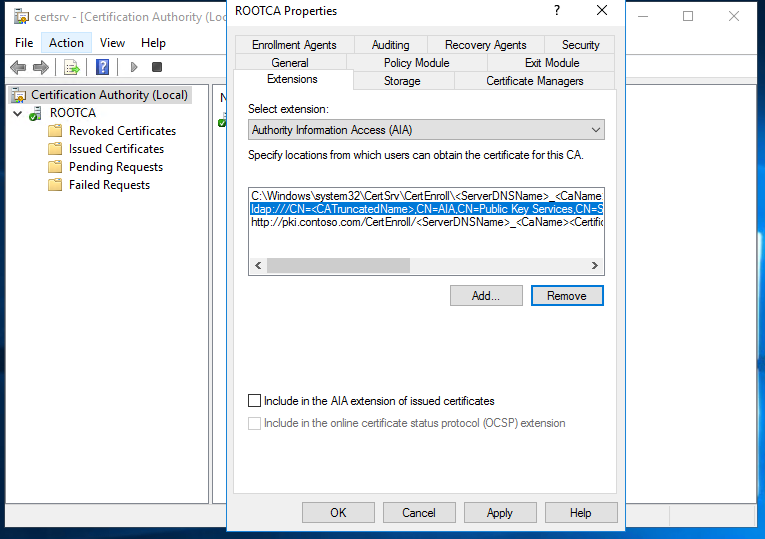
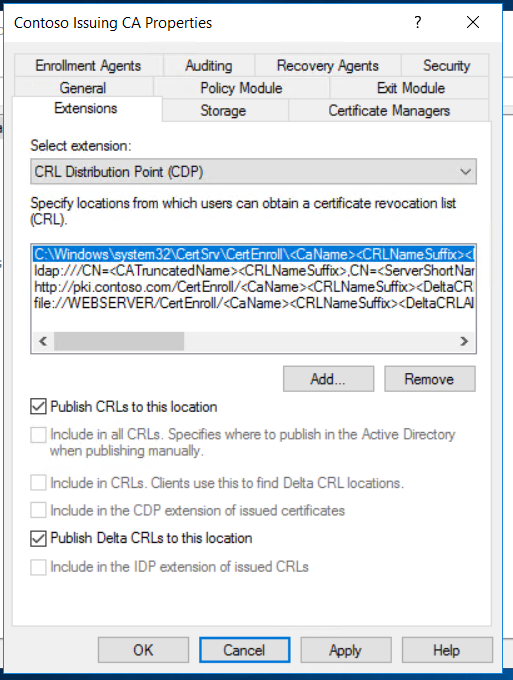
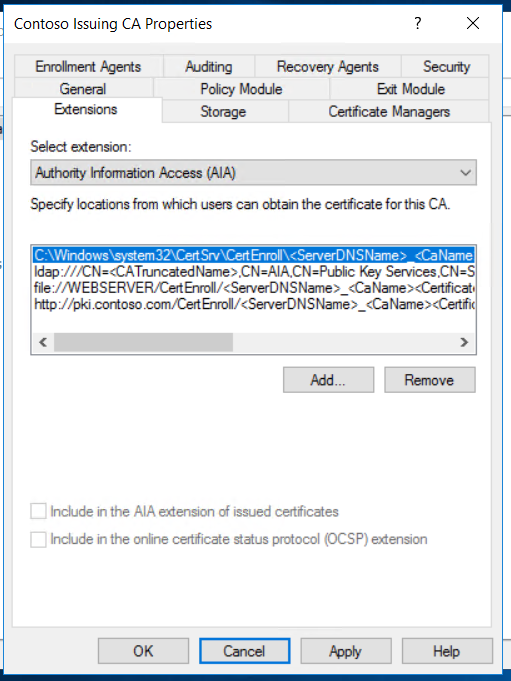
Once done, we can configure the location for CDP & AIA extensions.
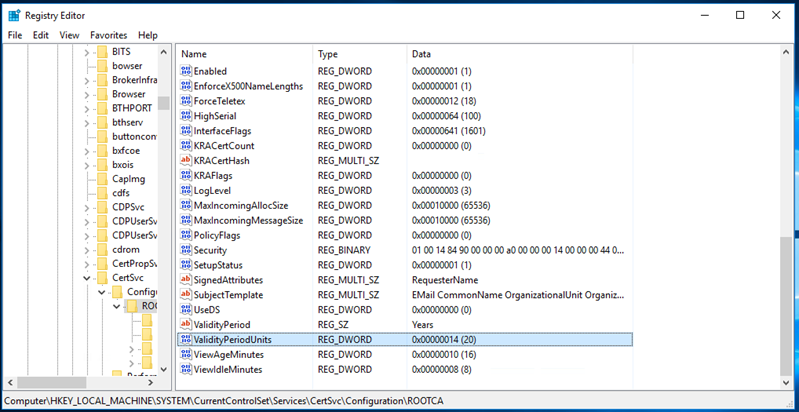
Since, Root CA will be offline, it is recommended to set the higher number for the Validity Period, for instance, 20 years, but modifying the registry value in the ValidityPeriodUnits registry key
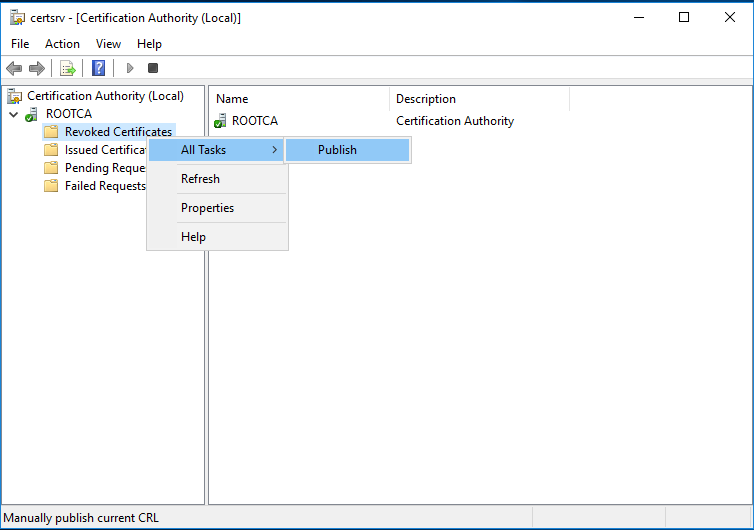
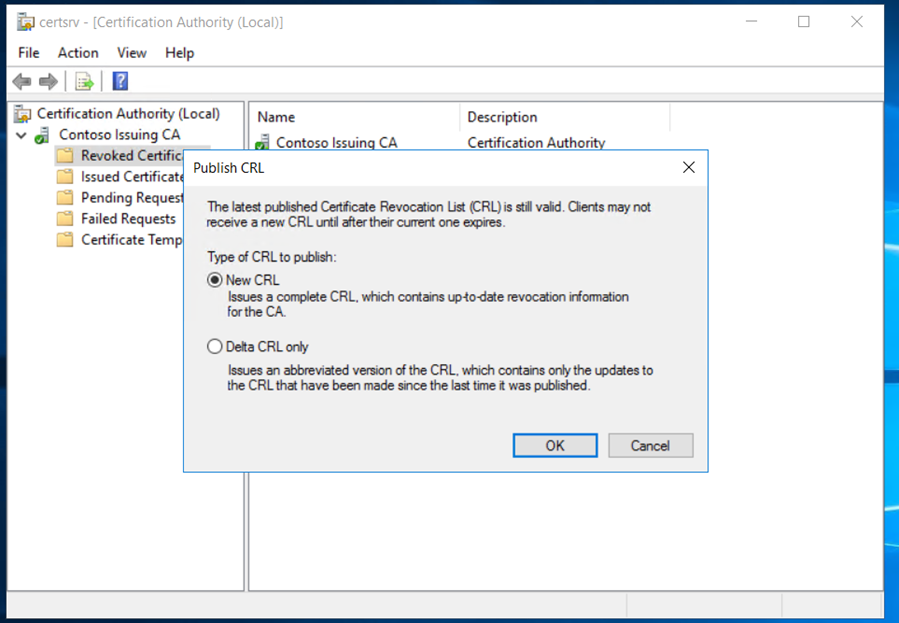
Publish the CRL
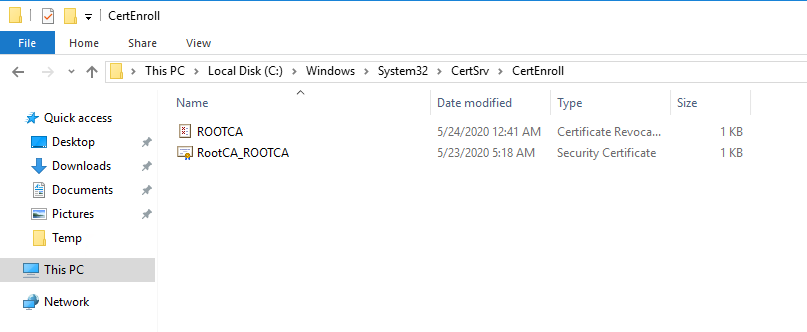
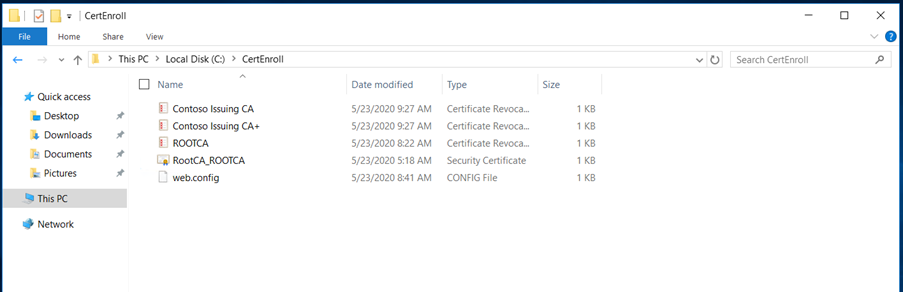
After the CRL generation, you can retrieve both CRL and AIA files on C:\Windows\System32\CertSrv\CertEnroll. You will need to copy these files for a later use a network share if your server is connected to a network or on USB drive if it is a physical server and not connected to a network.
We have now successfully deployed the Root CA and its operational.
Next step is to deploy the Enterprise Subordinate Issuing CA in Contoso.com. We need to prepare the Web server for the HTTP CRL publication for contoso.com and create the DNS record.
Forest A: Contoso.com
DNS record creation for pki.contoso.com
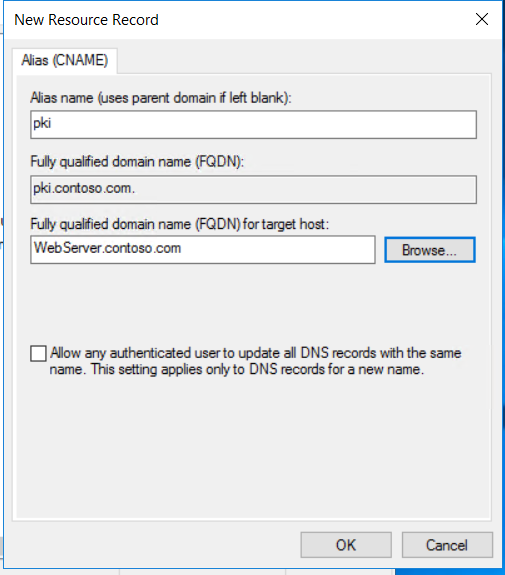
We must prepare HTTP Web Server for CDP and AIA Publication. Webserver will be joined to the domain contoso.com
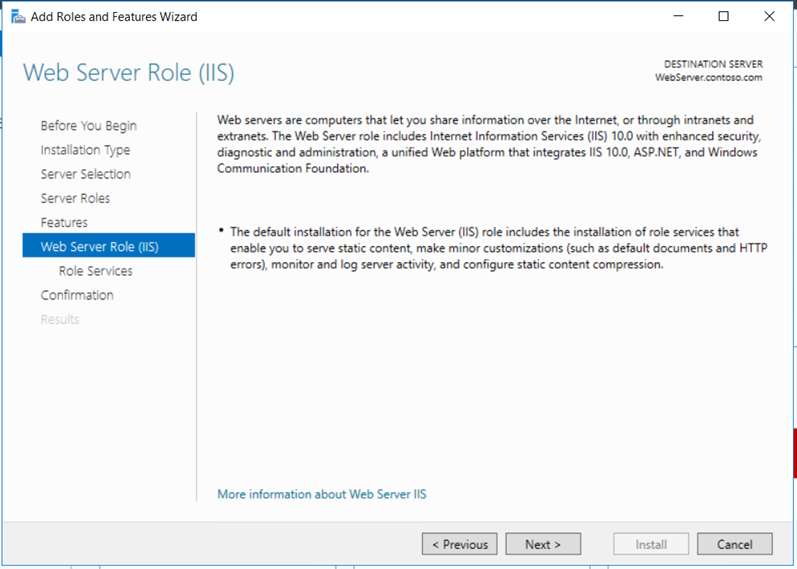
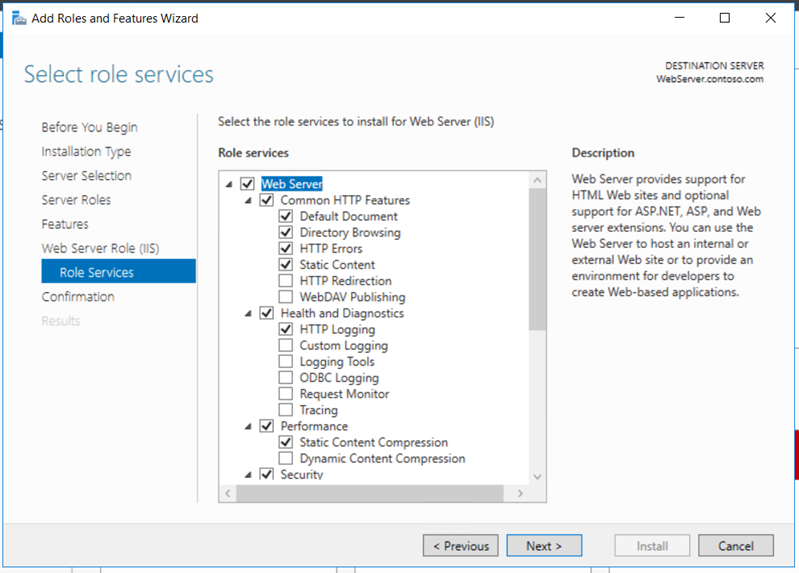
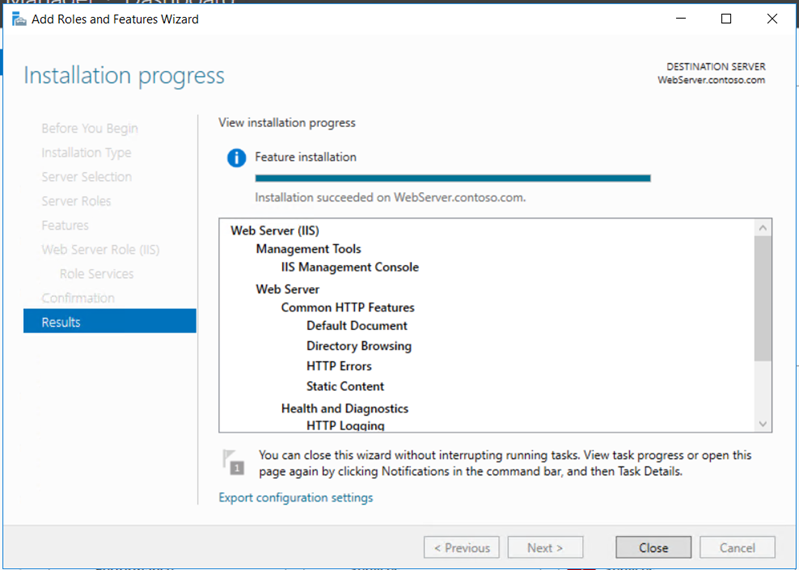
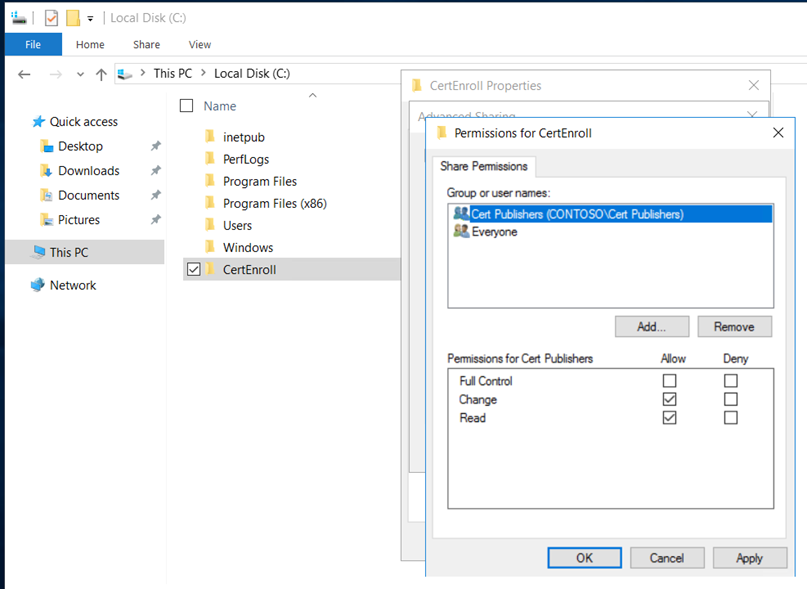
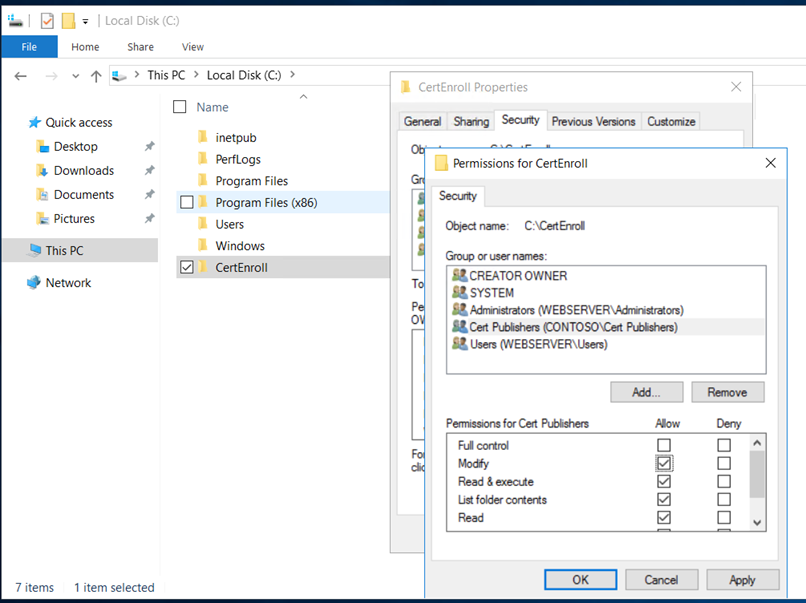
Create a folder “CertEnroll” and provide “cert publishers” change permissions on sharing and “modify” on the security permissions.
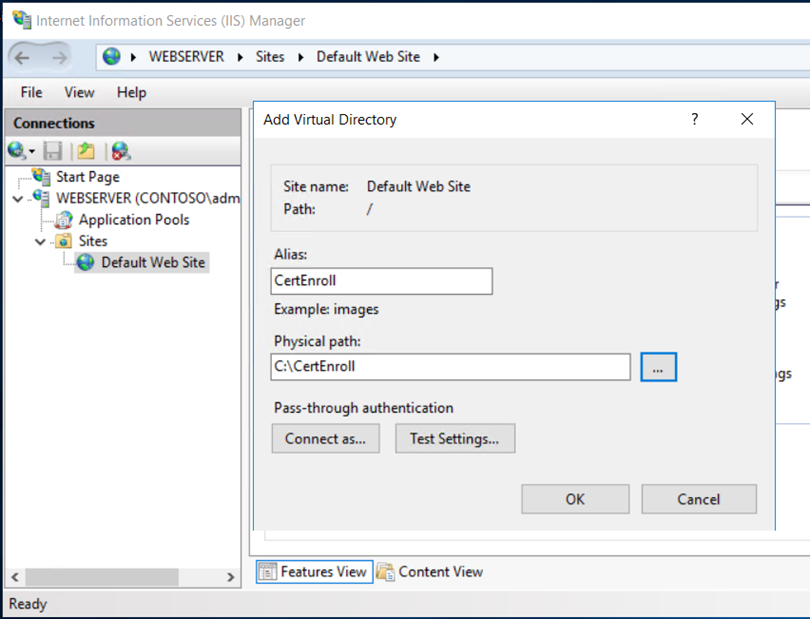
Open the IIS manager, create a new virtual directory and provide the details as below,
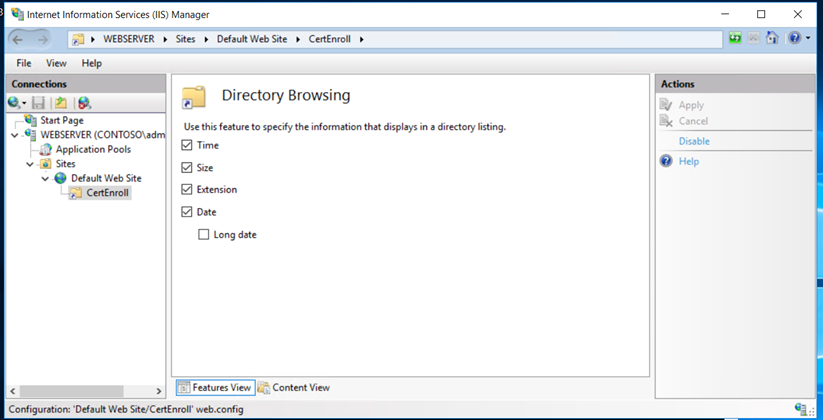
Enable the directory browsing,
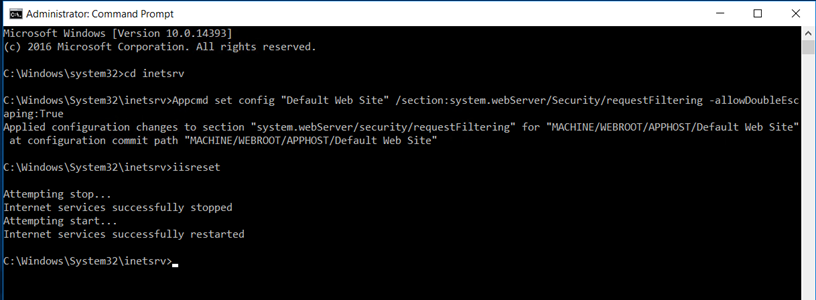
Enable the Double Escaping, this will allow the web server to host Delta CRLs
Now, it’s time to deploy the Enterprise Subordinate Issuing CA in Contoso.com. Before we install the roles, we must publish the Root CA certificate in the Contoso.com active directory so that the Issuing CA will trust the Root CA. This is one of the most important steps and this would avoid any errors while starting the Enterprise Issuing CA.
Copy the Root CA certificate and CRL and copy it to the Enterprise CA and run the below commands,
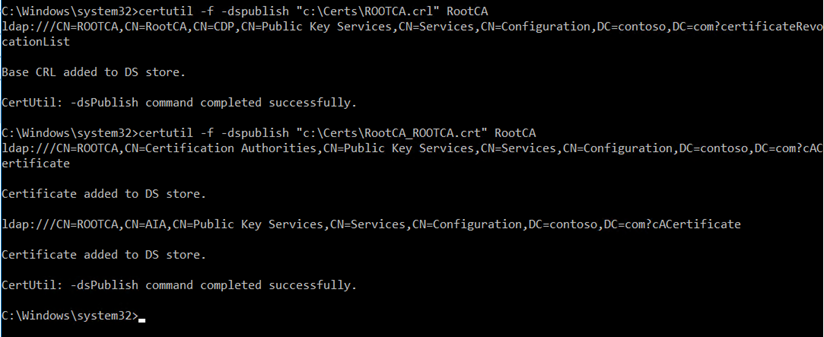
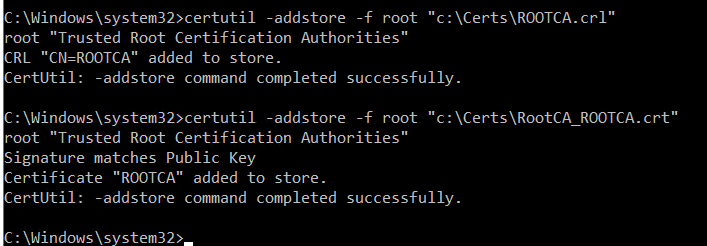
Once, it is published it the active directory. Add the certificates to the local store of the Enterprise CA
Install the role using the server manager,
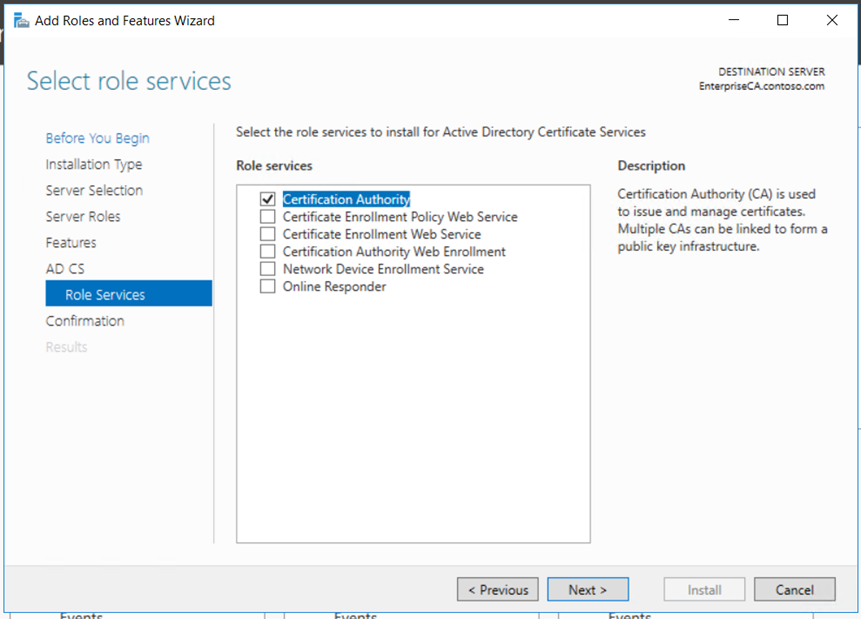
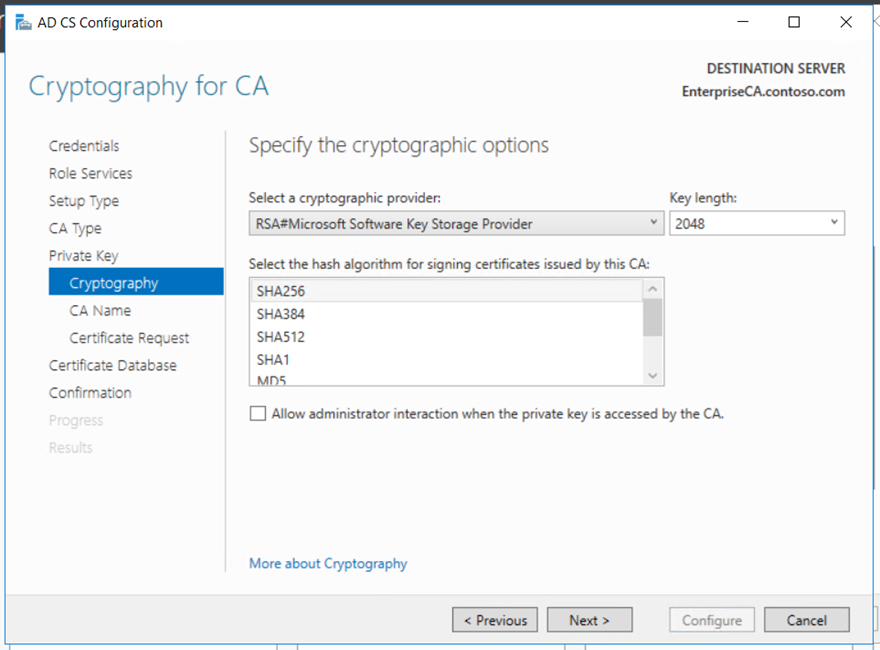
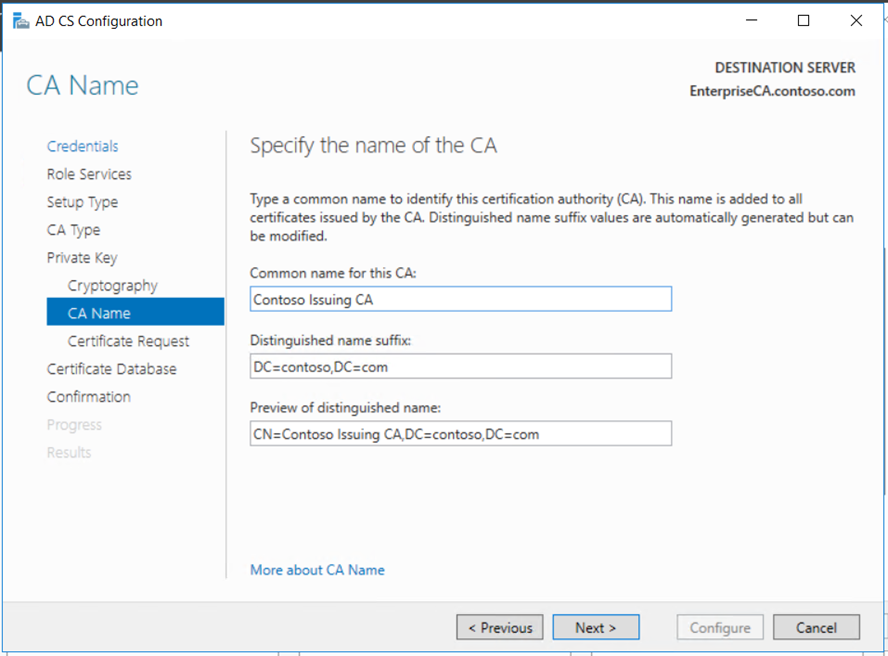
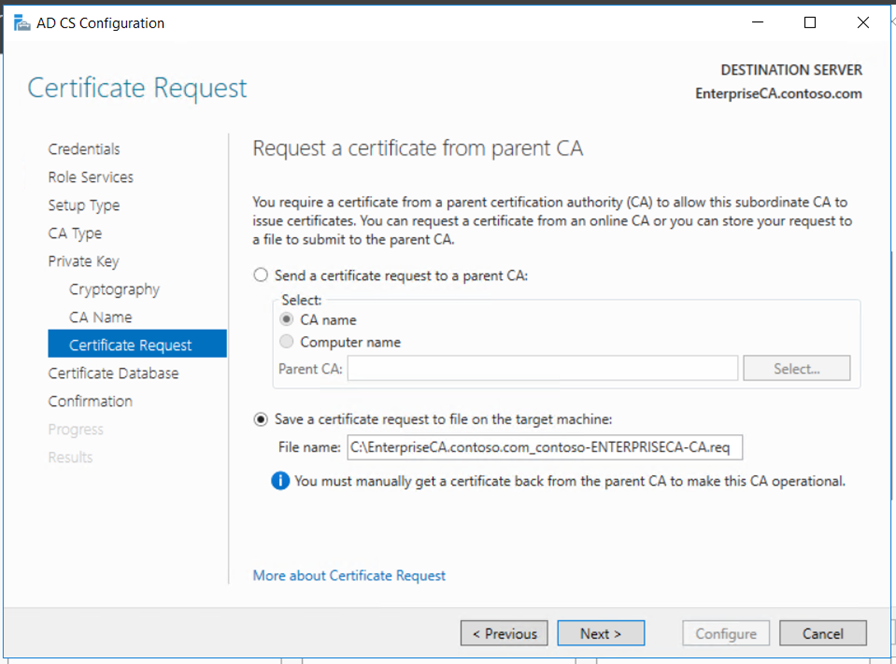
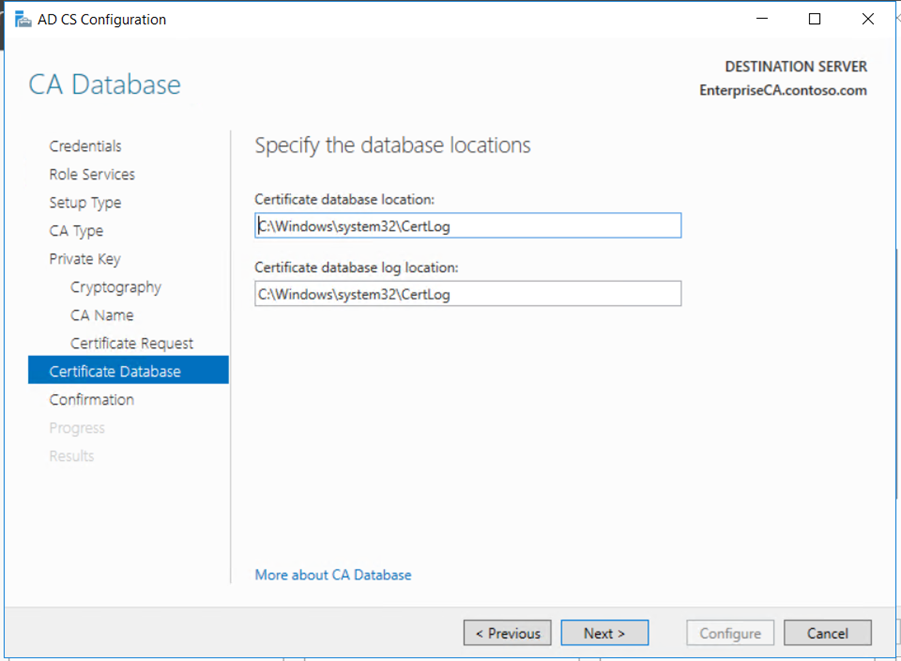
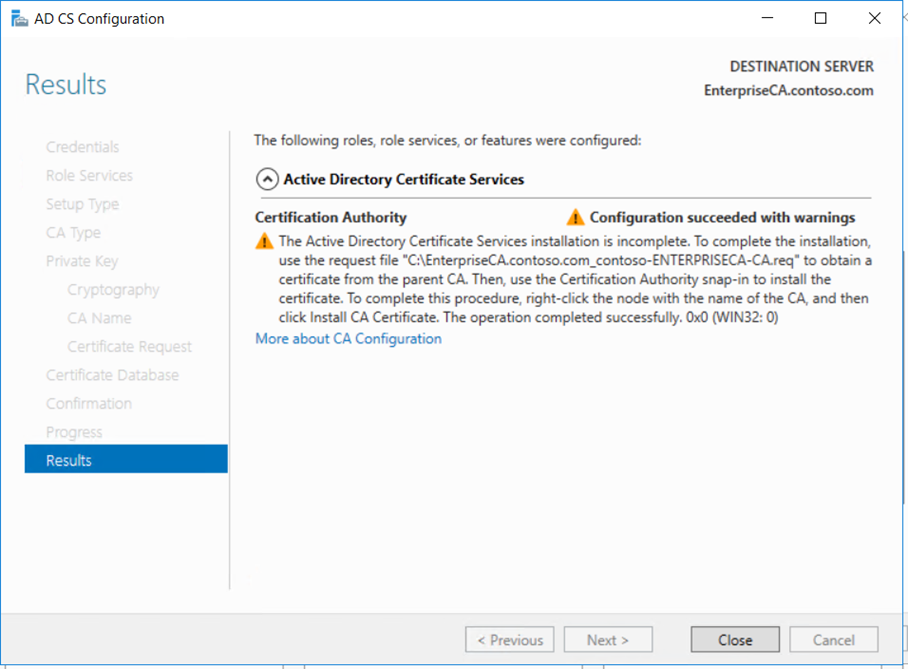
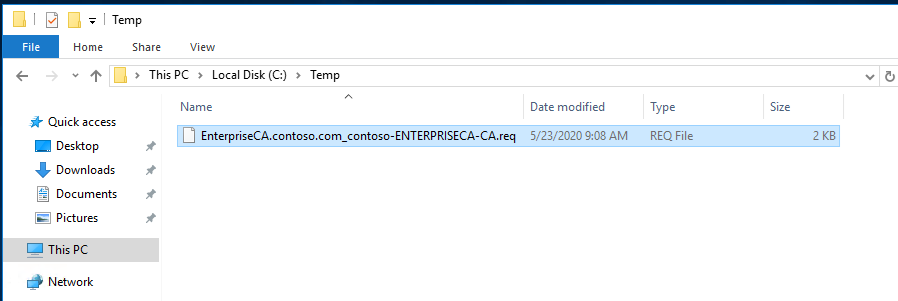
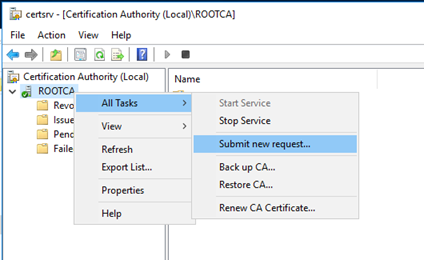
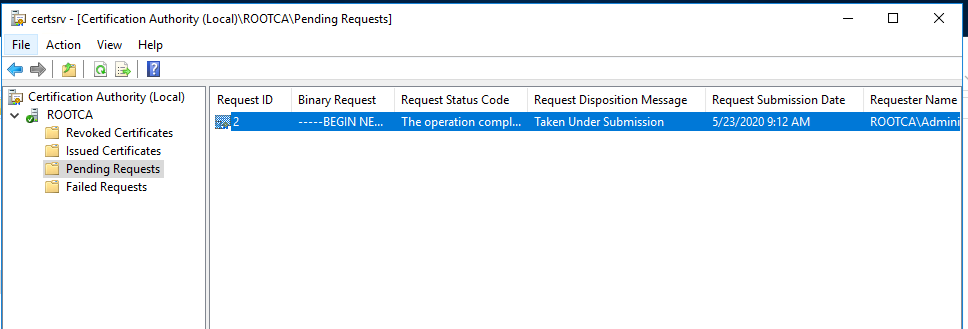
Copy the request file to the Root CA if it connected to the network or using USB. Submit the mew request to the Root CA and get the new certificate for the Enterprise Subordinate Issuing CA.
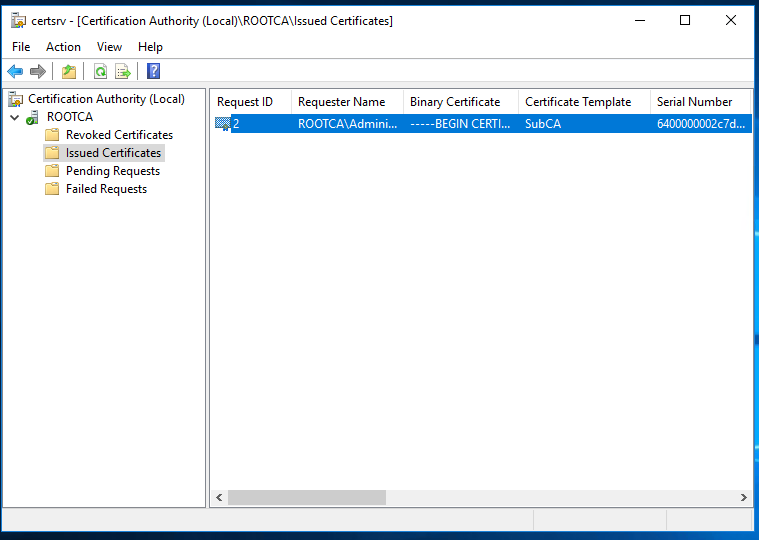
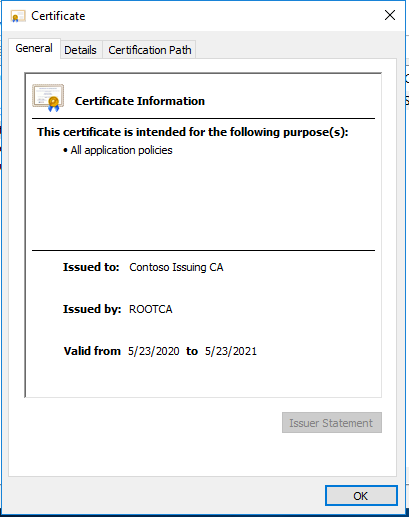
Copy the certificate to the Enterprise Issuing CA and install it
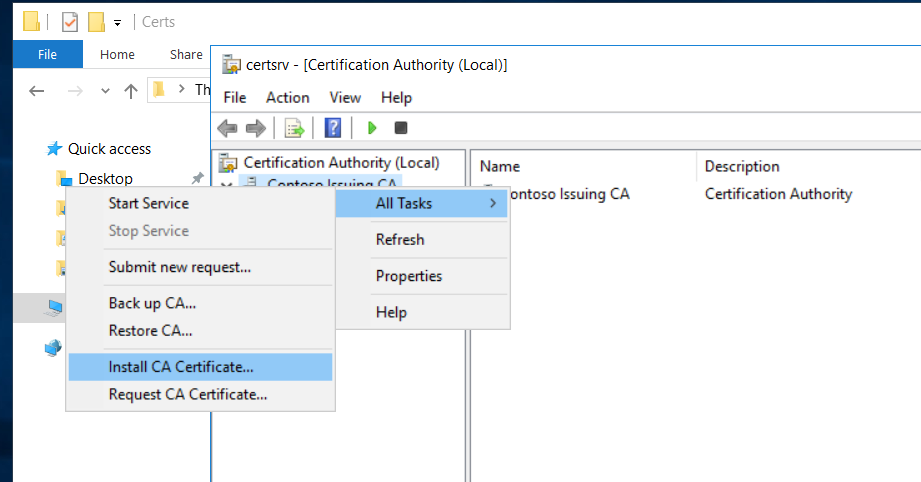
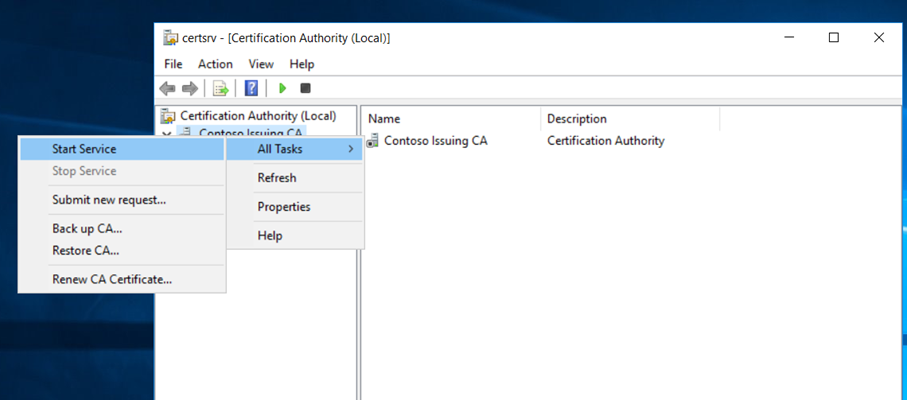
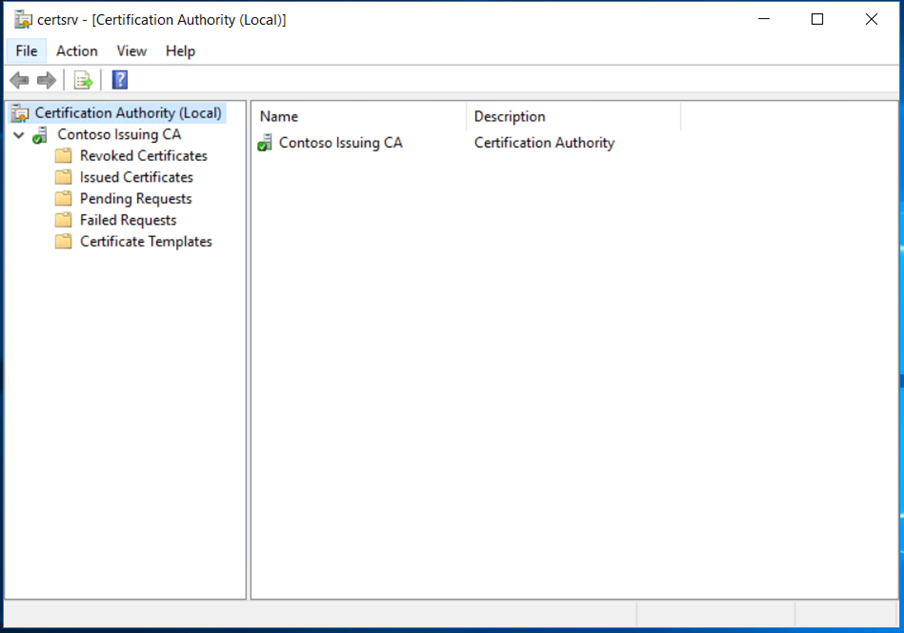
We have now successfully deployed the Enterprise Subordinate Issuing CA and its functional. We must do the post configuration tasks as we did for Root CA.
New location has been added to CDP & AIA extensions
Publish the CRL,
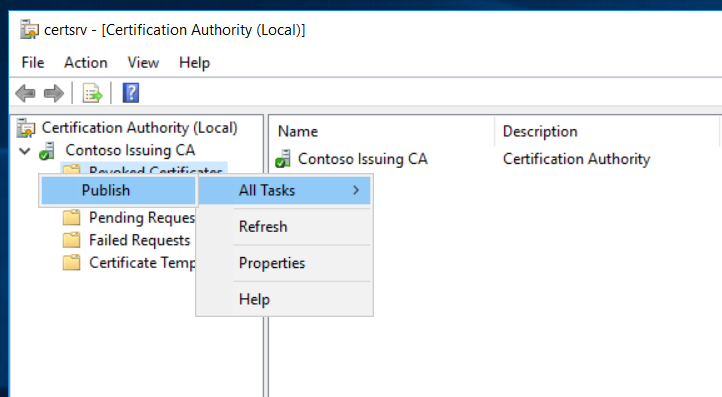
We can use the pkiview.msc to check the health of the PKI infrastructure,
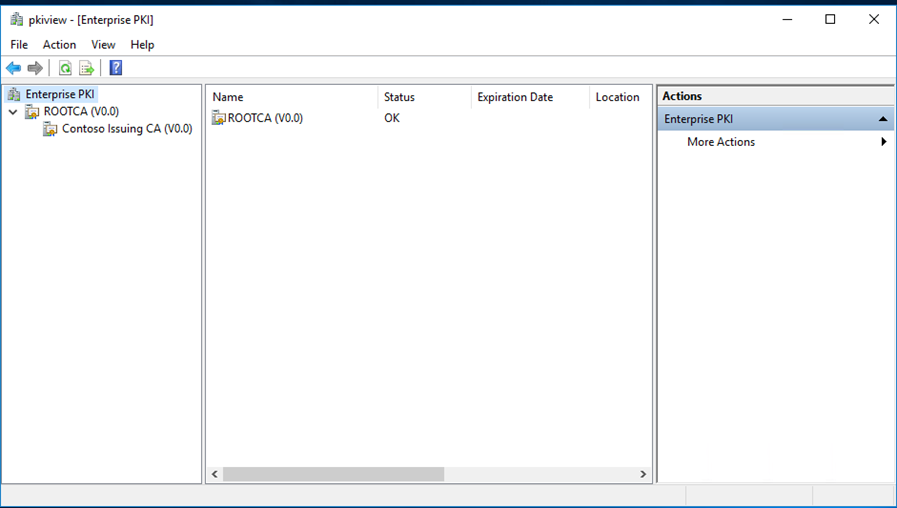
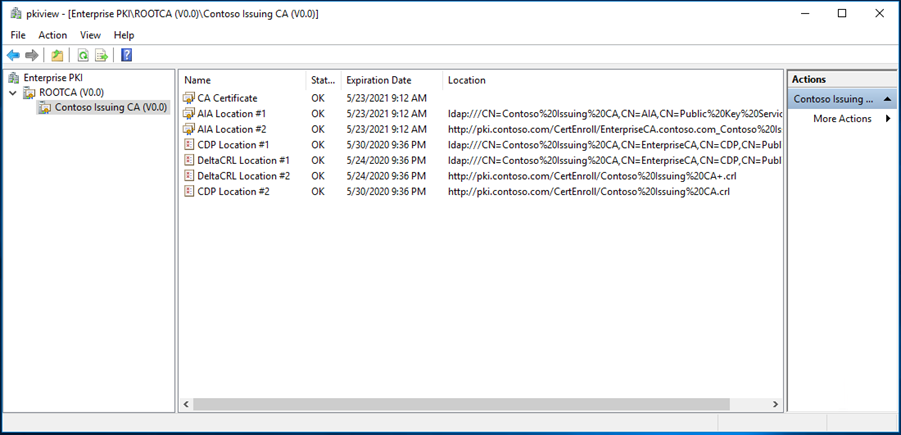
Finally, we have deployed the two-tier PKI in contoso.com successfully and by publishing the CRL in the web server.
Next step is to deploy the Enterprise Subordinate Issuing CA in CloudExchangers.com by using the Root CA will be continued in Part 2.
Happy learning!! 🙂
You are brilliant!
Really was benificial.
Many Thanks!